Introducing sendsecure.ly—a free and safe way to share your secrets

Do you need to share a password to your Netflix Amazon, Hulu, or Disney+ account with household members or roommates but don’t want this sensitive information in their text history? Have to share credentials or secrets, but don’t trust your coworker to delete the message from the office’s chat app?
The problem is that traditional communication channels such as SMS, email, Slack, or other chat apps leave behind a digital footprint, or paper trail, that could be exploited.
At Basis Theory, we’re making the internet more secure by making it simpler for developers to secure their data. Usually, consumer challenges such as these are outside our dev-first focus. Still, during a recent Basis Theory hackathon, a group of us saw an opportunity to create a truly secure and freely available solution that anyone can use to share sensitive data.
Introducing Sendsecure.ly
Sendsecure.ly ensures your passwords, API credentials, card numbers, etc. don’t exist in perpetuity within your friends’, family’s, and coworkers’ emails, SMS messengers, or chat apps. Instead, the web app allows anyone to share their sensitive data as a single-use undecipherable link that you can share with whomever. Opening the link will reveal the secret before being promptly destroyed.
How to use sendsecure.ly
Let’s say you have a piece of sensitive text you wish to share with a friend or coworker. For example, this could be:
- A password to a subscription service, such as Netflix, Amazon, or Spotify, may need to be shared with a partner or other household members.
- Personally identifiable information, such as an SSN or passport number, may need to be sent to your company’s HR department.
- API Keys or credentials used for authentication to a software system may need to be shared with a coworker.
Regardless of the type of text, sendsecure.ly can share it in 3 easy steps.
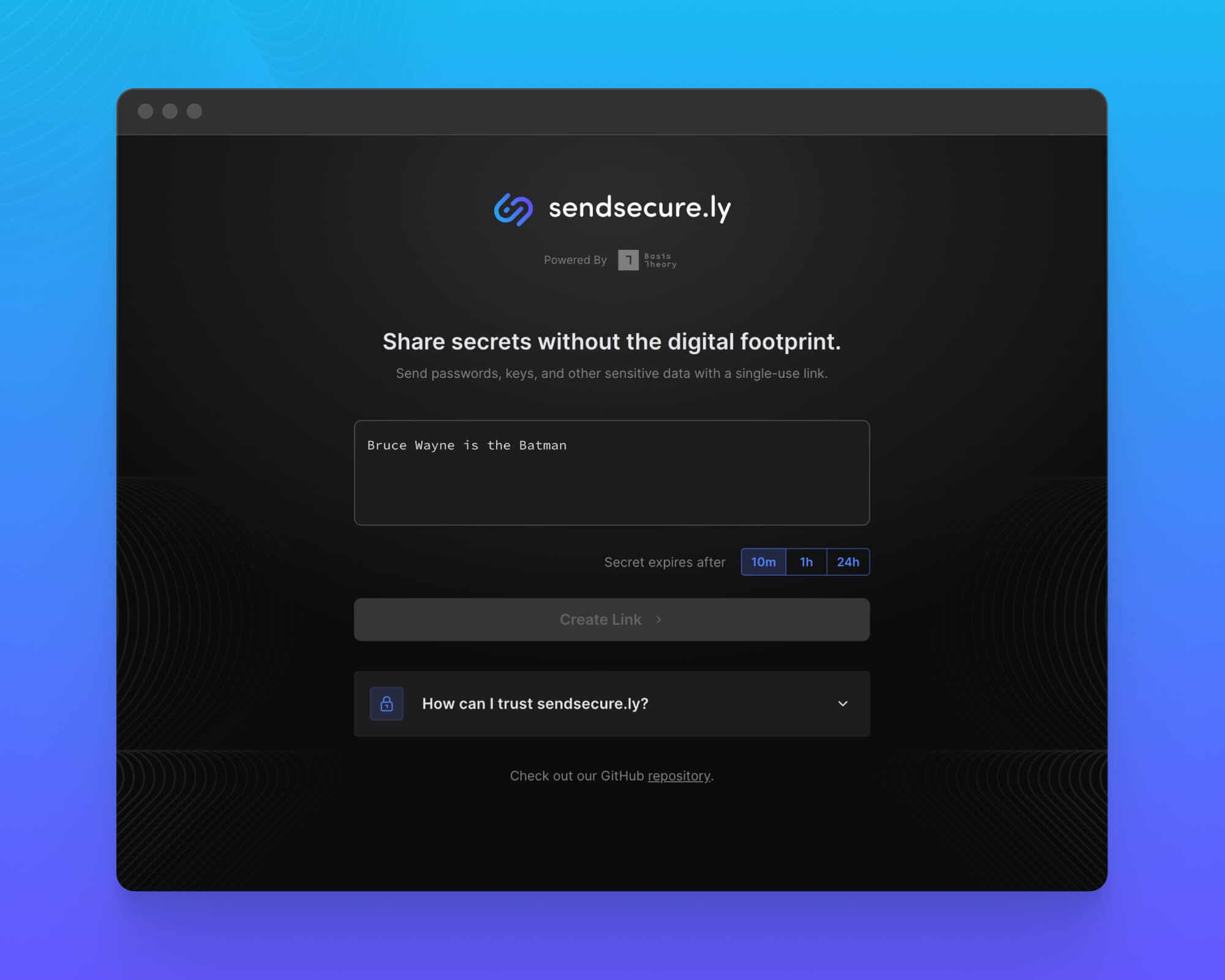
Step 1: Secure your secret
Once at sendsecure.ly, enter your sensitive text into the form and choose how long the secret should be available before expiration. You can choose between 10 minutes, 1 hour and 24 hours.
Click the Create Link button to secure your text and generate a single-use link.
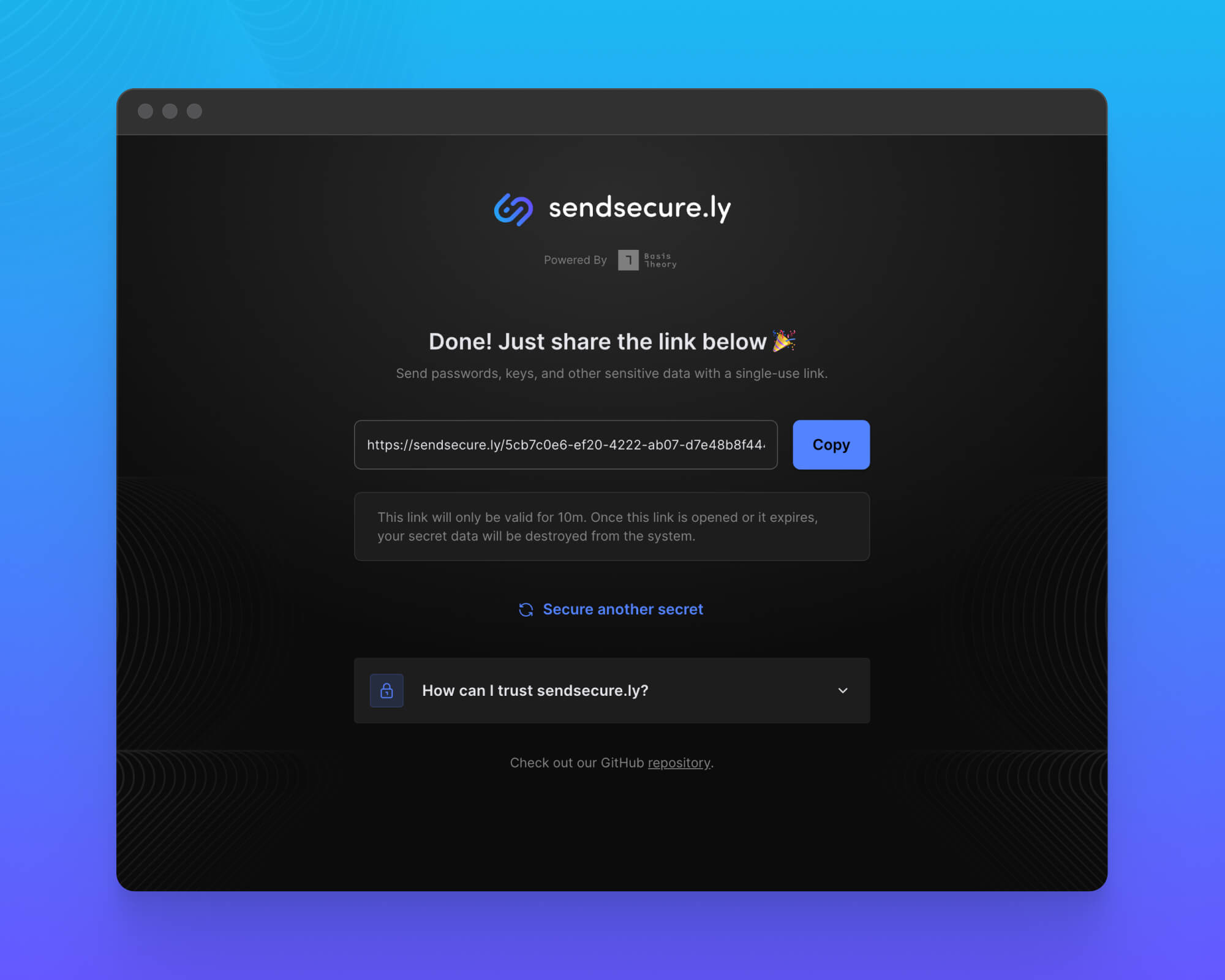
Step 2: Send your link
Copy the generated link and share it privately with your intended recipient. This link is safe to share directly with someone you trust, but be careful not to share it publicly or let anyone else see it.
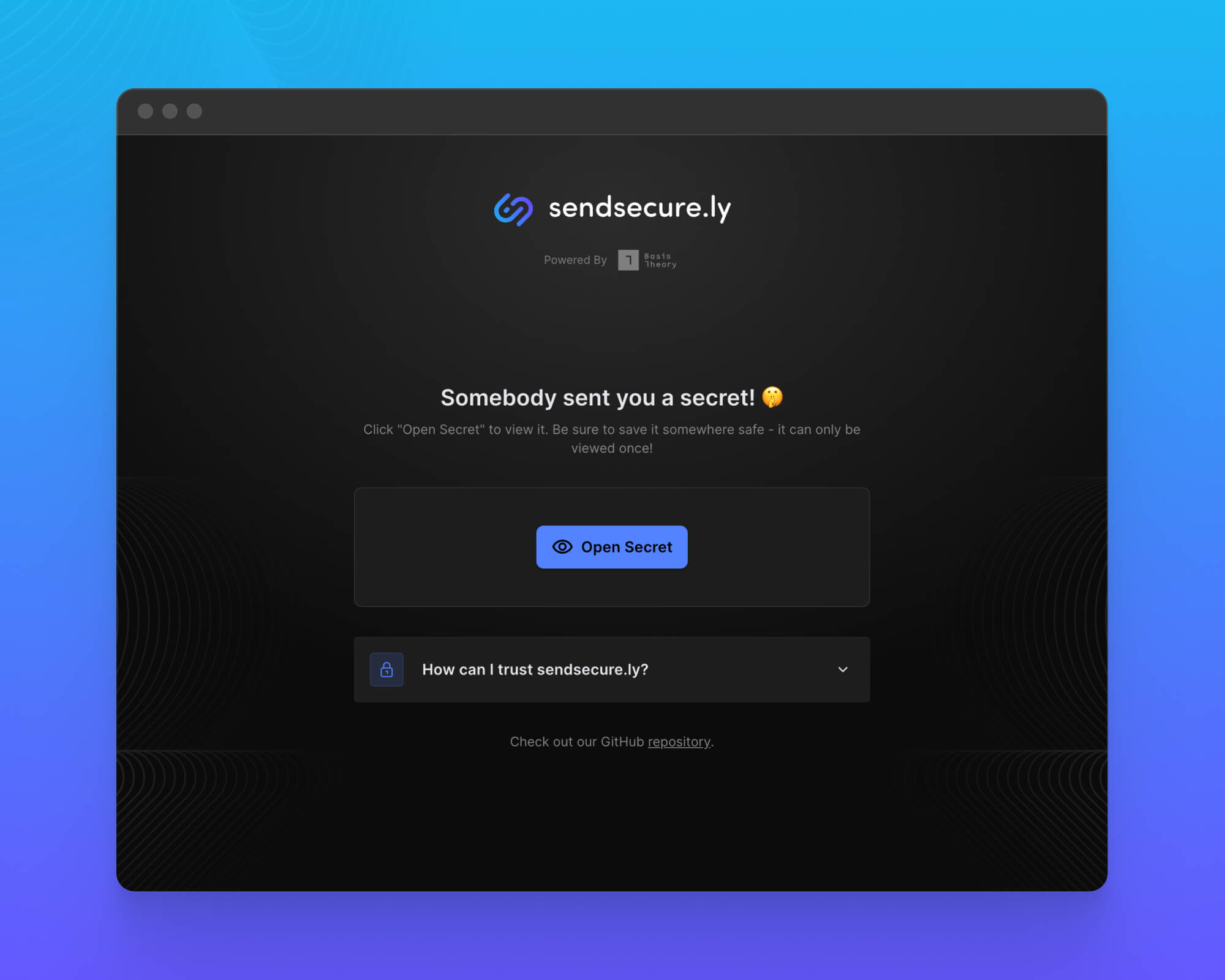
Step 3: Recipient retrieves your secret
Once you’ve shared this link with someone, they may click the “Open Secret” button. This will reveal the original secret information you entered and immediately invalidate the URL for future use.
IMPORTANT: The data cannot be retrieved again, and the underlying sensitive information is purged from the system immediately after it is retrieved.
How is the original text secured?
Sendsecure.ly does not store the original text and, instead, uses TLS 1.2 to transmit it to Basis Theory. Basis Theory then encrypts and stores this text in its PCI Level 1 data vault and SOC 2 compliant environment before generating and returning a token to sendsecure.ly.
“A Token is a non-sensitive identifier that references sensitive data and can be shared or exposed without any risk of exploitation.”
Even supporting information, such as the secret’s TTL, is stored using Basis Theory and is attached to the token as metadata.
Mitigating the risk of exposure
As stated, anyone who obtains access to the shared link will be able to retrieve your secret information. There’s also the risk that when sending this link through communication channels—such as SMS or a chat app—trace information of your message may be left on third-party servers. Bad actors could theoretically capture this.
Sendsecure.ly helps in two ways:
- The link can only be used one time. Once revealed, Sendsecure.ly ensures Basis Theory destroys the original text.
- The link is only valid for a short amount of time. Each secret has a configurable TTL from 10 minutes up to 24 hours. Once expired, sendsecure.ly ensures Basis Theory destroys the original text.
Built using Basis Theory
Sendsecure.ly is a Next.js application written using TypeScript and built upon the Basis Theory platform. All interactions with the Basis Theory API are performed using the JavaScript SDK, and executed within the Next.js backend API.
For example, when a user enters a secret, sendsecure.ly creates the token through the SDK using this code:
export default async (req, res) => {
const bt = await new BasisTheory().init(env().BT_API_KEY);
const token = await bt.tokens.create({
type: 'token',
data: req.body.data,
metadata: {
ttl: req.body.ttl,
},
});
res.status(200).json({
id: token.id,
ttl: req.body.ttl,
});
};
The SDK also makes it easy for sendsecure.ly to retrieve the token data and delete the underlying token in just a few lines of code:
export default async (req, res) => {
const bt = await new BasisTheory().init(env().BT_API_KEY);
const { id } = req.query;
const token = await bt.tokens.retrieve(id);
...
await bt.tokens.delete(id);
...
res.status(200).json({ data: token.data });
};
If you’re interested in diving deeper into how we built sendsecure.ly, you’re welcome to check out the entire codebase in our GitHub repository.
Go tokenize!
Sendsecure.ly is free to use for your personal or professional secret sharing needs. If you have ideas to improve the service, throw them in our slack community or contribute to the GitHub repo.
If you’d like to learn more about building secure applications using Basis Theory, check out our Developer Documentation. Ready for your own secure environment? Create a free account.
.png?width=365&height=122&name=BTLogo%20(1).png)




-Dec-13-2022-06-27-12-2630-PM.png?width=50&name=62507e98e39fbe12913a3198_nathan-loading%20(1)-Dec-13-2022-06-27-12-2630-PM.png)
