What are Reactors and Reactor Formulas?

What challenges do Reactors solve?
Processing, analyzing, and sharing (i.e., “using”) your sensitive data brings additional challenges to development outside of merely securing and managing it. Reactors solve a few primary problems.
Sensitive data triggers complexity. Card data, for example, is required to be housed and used in a secure, tested, and governed card data environment (PCI mandates up to 224 security and risk controls). This can make it hard for different parts of your codebase to utilize card data directly. While this scope triggers one of the hardest and most costly problems to solve and maintain for developers, it doesn’t just impact those handling card data. Personal identifiable information, deposit account information, and even confidential business data, like pricing, inventory, and logistical information, can trigger internal compliance policies to mitigate the risk posed by its use.
Sensitive data’s risk constrains use. As mentioned above, internal or external compliance requirements constrain the circumstances, environment, and actors that can use sensitive data. Traditionally, this has limited its use to the primary purpose for which it was gathered (e.g. SSN for identity verification). This “chilling effect” has limited organizations' ability to provide valuable product functionality, user experiences, partnerships, and insights.
Sensitive data requires privacy. Limiting access shrinks the threat surface area posed by sensitive data. OWASP’s Top Ten, ”a standard awareness document for developers and web application security,” suggests organizations classify and assign impact levels to its data to prevent direct or indirect abuse of its sensitive data. While the assignments of these classifications and impact levels are considered business decisions, applying and enforcing them at the data property level can take days to months to implement—depending on the size of the team and codebase.
What are Reactors?
A Reactor is a serverless compute service. It allows developers to execute Node.js code, called a Reactor Formula, against your tokens within a dedicated Basis Theory environment, called a Tenant. Invoking a Reactor, which can be done from any system that can make an HTTPS request, allows developers to perform virtually any operation against their data while keeping it isolated from your existing application and systems.
💡 Node.js compatible Reactors are currently in private beta - reach out if you’re interested in using other languages or access to our Node.js environment.
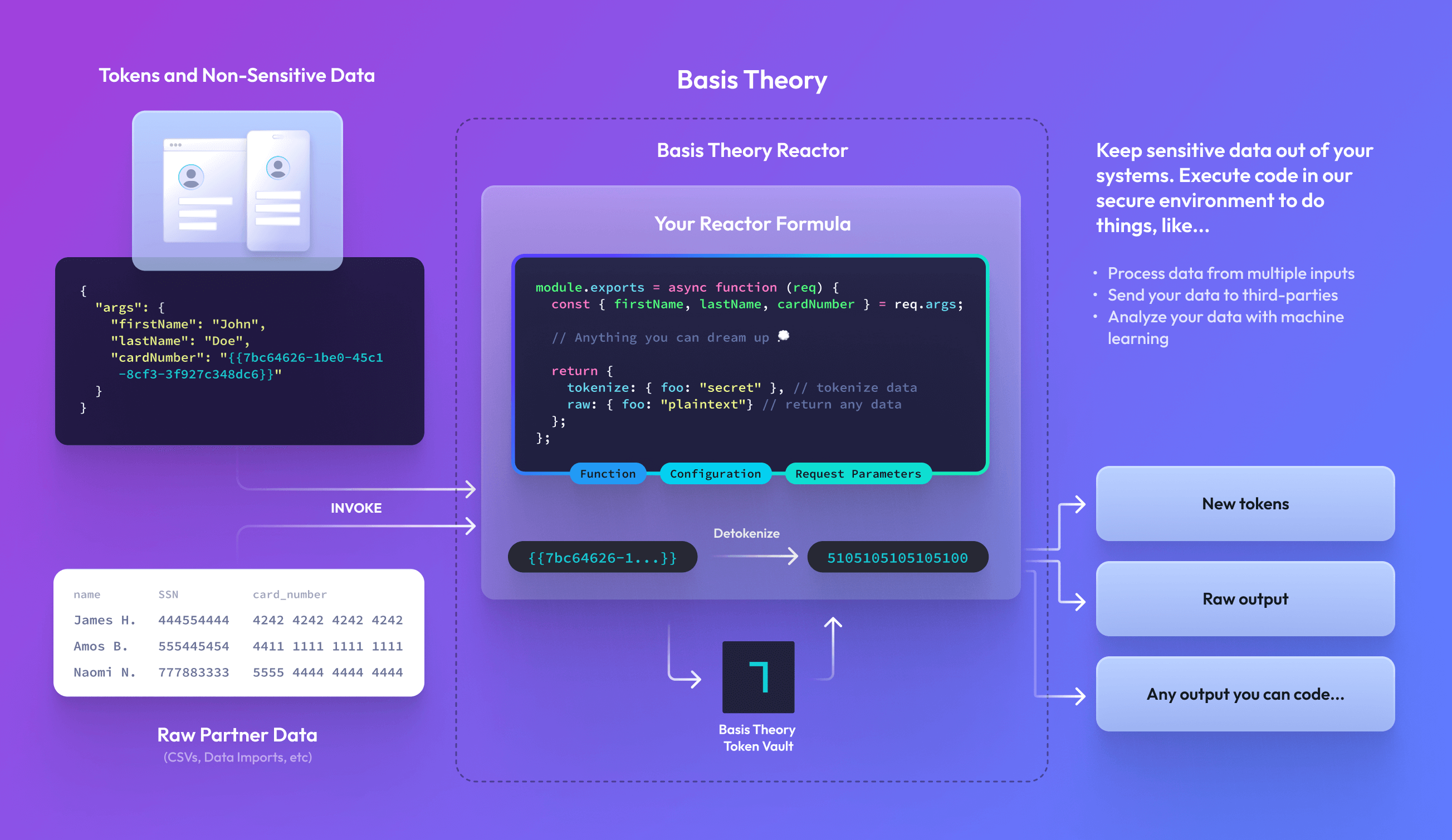
How do Reactors make building secure and compliant applications simpler?
If organizations storing sensitive data within Basis Theory’s environment (called a Tenant) inherit its PCI Level 1 and SOC 2 security controls and protections, the same can be said about Reactors. When using a Reactor, developers abstract the extra work required to build out and maintain a PCI environment. It also provides developers a centralized and contained location to host and execute serverless functions that we call Reactor Formulas (or Formulas).
💡 Reactor Formulas can be seen as having capabilities and benefits similar to AWS Lambdas, Azure Functions, or GCP Cloud Functions.
How to Use Reactors:
Developers use Reactors to process, analyze, and share their data and can be used to ingress or egress data to and from your Tenant. Meanwhile, Reactor Formulas provide the instructions.
There are two types of Reactor Formulas
- Use one of Basis Theory’s pre-built Official Reactor Formulas.
- Create your own Custom Reactor Formula (in Beta)
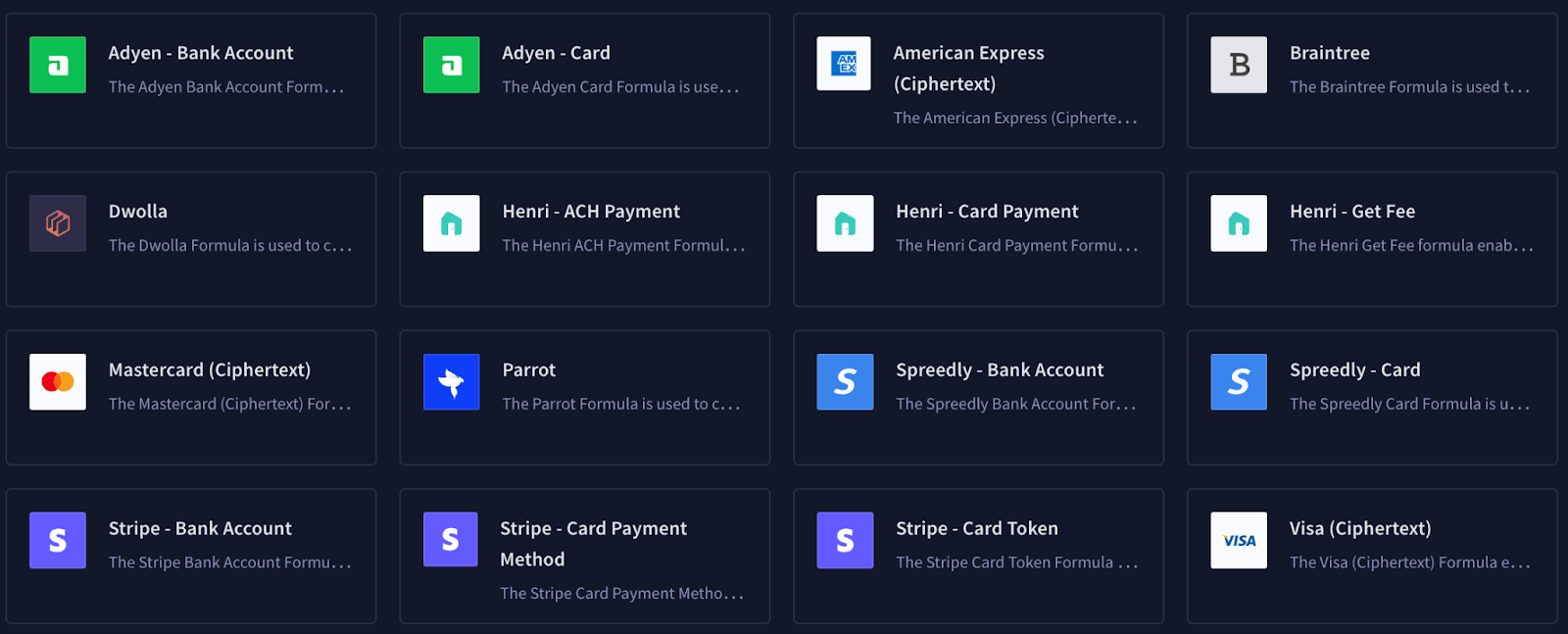
Official Reactor Formulas
Basis Theory has built numerous compliant and secure Reactor Formulas you’re able to use out of the box, like templates. Using an Official Reactor has a couple of benefits:
- Allow developers to send and receive data with third-party services or perform common functions quickly
- Ensures data is not exposed to your organization and that it is used as intended
You can also fork these templates as foundations to write your own custom code.
Private Beta: Custom Reactor Formulas
We set out to design Reactors to enable the kind of flexibility and utility developers would generally expect when interacting with data within their systems. Custom Reactor Formulas allow organizations to do just that. By deploying their own code within a Reactor, developers can create bespoke operations, derive user insights, or share outputs with third parties—all without exposing their organization’s systems to sensitive data. For example, you may want to:
- Create a PDF with Social Security numbers
- Generate a text file and transfer it to another server over SFTP
- Run analysis on your sensitive data and report results
- Anything a traditional serverless platform would enable
Join our Slack community and to request access to Custom Reactor Formulas in the #beta channel.
How can I get started?
Everything we just showed is free to access and use, and you can get started in minutes. Feel free to register, explore using Reactors within your own Tenant, and give us feedback in our Slack community.
.png?width=365&height=122&name=BTLogo%20(1).png)



.jpeg)

