February 2023 Changelog

After the numerous improvements the team released in January, we spent February heads down on a few initiatives to make progress toward developing a more complete platform to address compliance needs. We believe in the idea that sensitive data can be used as easily as regular data, and our platform enables companies to focus on creating value for their customers, rather than worrying about compliance concerns.
Here’s how we spent our time in February.
Launching Asynchronous Reactors
We received feedback that users wanted to process larger files of sensitive data than our platform could handle. In response, we increased the reactor compute time from 10 seconds to 3.5 minutes. To achieve this, we switched our reactors from synchronous to asynchronous calls.
This change enables the platform to handle longer running batch jobs and file transfers while ensuring safe data import into Basis Theory. Learn more about reactors here.
This enhancement also opens the doors for additional possibilities, including:
- Running time-consuming algorithms against sensitive data, or nightly jobs such as:
- Long running synchronous API Calls
- Card Token Synchronization through POS & e-commerce
- Financial Reporting
- Fraud Detection Analysis
- Data Auditing
To better support these longer running calls, we also built a way to identify whether the call was still in progress by creating a system to support idempotency, which will prevent unintended behavior when making repeated requests. To prevent collisions, a client can provide a unique Idempotency Key when making a POST, PUT, or PATCH request to the API endpoints.
The response to the first successful request will be returned for subsequent requests with the same Idempotency Key. Idempotency Keys and their corresponding results are deleted after 24 hours.
Reveal Sensitive Data Securely and Without Scope
We’ve written about Reveal in the three most recent changelogs, but we want to call it out one more time. If you’re looking for the complete Reveal documentation, you may use our Issue and Display Credit Cards blueprint. Reveal is fully native in iOS & Android as well as web.
Use our SDKs to jumpstart your implementation.
Fingerprinting
To improve performance in token creation, fingerprinting is now opt-in for all new tenants created. To flag and take action on duplicate data you can use fingerprinting like before by passing the deduplicate_token parameter. Alternatively, you can now enable fingerprinting at the tenant level, as shown below.
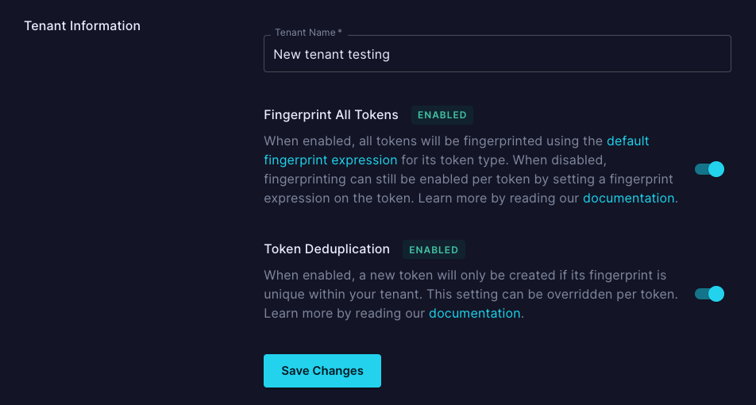
All current paying customers have received correspondence regarding these changes, but if you have any additional questions, please reach out or learn more here.
Other Releases, Fixes, and Improvements
- Added enableCopy card details functionality for Reveal
- Fixed warning with iOS elements
- Fixed performance when utilizing the same token multiple times in a proxy
- Small performance enhancement across all authenticated endpoints
- Calling proxy via basistheory-js now callable with no path
.png?width=365&height=122&name=BTLogo%20(1).png)




